Take control of your company's security starting at $1495
With Protection C4: the Cybersecurity and Compliance Control Center





“Data breach,” “ransomware,” “Law 25”: how many times have you come across these terms in the news over the past few months? The pressure is mounting on organizations, the primary targets of cybercriminals, which must now comply with increasingly stringent regulations.
The question is: how do you protect your company’s data? Do you go offline and return to using paper?
That might work, but we prefer an approach that doesn’t hinder your productivity 😊
Protection C4 was designed for YOU. In short, this risk management SaaS platform (Software as a Service) will help you assess your security maturity level and provide a tailored action plan to fit your needs.
Together, we’ll make life harder for hackers by making your organization more secure.
Your data's security is vital for your organization’s success. Act now to safeguard it.
Data breaches and ransomware attacks are well-known cyber risks. But do they really pose the greatest threats to your organization? With Protection C4, uncover the specific threats targeting you and strengthen your cybersecurity.
With Protection C4, get recommendations tailored to your organization’s specific needs. Track the progress of your cybersecurity score and compare it with other companies in your industry or of similar size.
Protection C4 prioritizes your recommendations based on their criticality, your budget, and the time required for implementation. You’ll know exactly where to start to efficiently strengthen your cybersecurity.
Protection C4 enables you to understand the threats specific to your organization, plan, visualize, and implement your recommendations. Your dedicated cybersecurity advisor is finally within reach.
With Protection C4, you can accurately assess the cyber risk level of each of your digital assets and ensure continuous monitoring over time. Whether it’s your website, Wi-Fi networks, Microsoft 365 environment, server or computer infrastructure, or even compliance with Law 25, everything is taken into account.
This targeted view of your security will allow you to focus your efforts, increase efficiency, and collaborate easily with all the providers involved in your technological ecosystem.

Once your digital assets have been evaluated, you’ll receive a detailed report highlighting the risks and vulnerabilities specific to your organization. However, not all vulnerabilities carry the same weight or have the same impact on your business. That’s where Protection C4 comes in to provide clarity.
Each vulnerability is presented with:
With Protection C4, you gain a comprehensive and understandable view of the risks, allowing you to better manage them.

Once you have a comprehensive view of the risks related to your assets, that’s when the magic happens. Protection C4 provides you with a custom action plan, prioritized based on a return on investment (ROI) calculation. This calculation takes into account the risk level, effort, and budget required for each correction.
With Protection C4, you know exactly where to start to strengthen your cybersecurity efficiently, without wasting time.
Working with external providers, such as an IT provider (MSP)? Assign them tasks with a single click and collaborate hand-in-hand to build a business more resilient to threats. Together, you’ll make it harder for hackers by reinforcing your organization’s resilience to cyber threats.

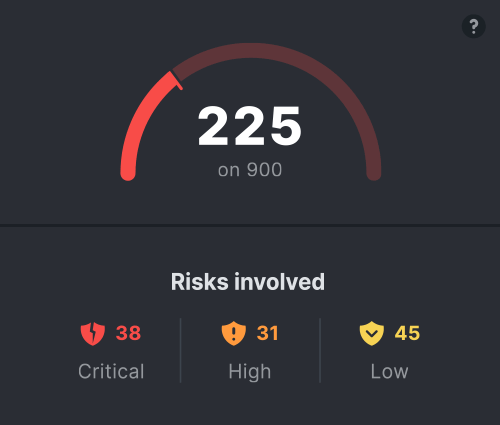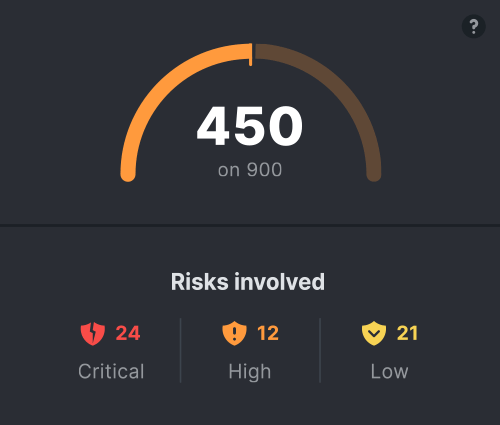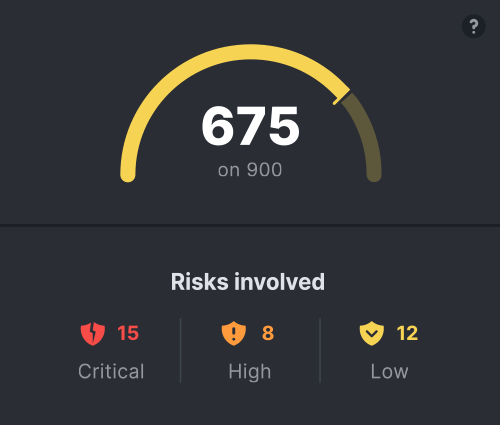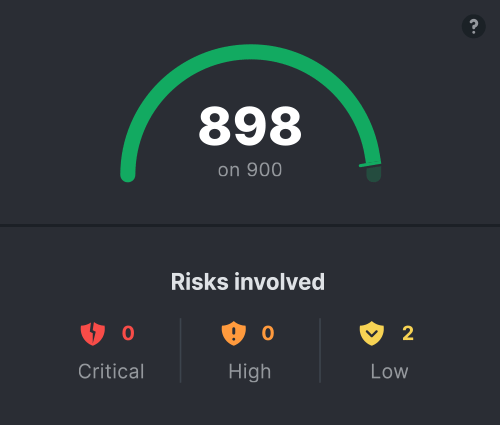
With Protection C4, you have a powerful tool: your security score. Similar to a credit score, the security score ranges from 0 to 900, allowing you to track its evolution over time and compare it with other companies in your industry or of similar size.
This score, based on the value of your digital assets and the risks in your environment, gives you a clear and instant view of your cybersecurity status.
Every action taken to correct a vulnerability improves this score, allowing you to monitor the progress being made. It’s a motivating indicator for your teams, who can see the positive impact of their efforts in real-time and become more engaged in protecting the organization.
This score turns into a dynamic dashboard, guiding your teams toward clear and measurable goals, while boosting their motivation to achieve an even higher level of security.

It’s difficult to constantly monitor the actions of every member of your team in Microsoft 365, which can expose the entire organization to risk. Thanks to our integration, Protection C4 constantly monitors the security posture of your environment and provides you with concrete recommendations for minimizing threats.
To help us have a greater control of our security, we are highly interrested in the Protection C4 platform being developed by Cyberswat Group. We can see how this tool will allow us to be more efficient and proactive in the assessment and monitoring of our risks, thanks in particular to its dashboard that gives an overview of our cybersecurity risks. Of particular interest is the ability to assess risk and prioritize it based on financial impact.
Nom d’un des clients